[Urgent: Crypto Phishing][MetaMask Users] Take Action to Protect Your ETH/EVM Portfolio
Stop Phishing Before It is too Late!
There is so much phishing in crypto, and it is becoming rampant. It not only destroys families (losing all of the funds in ETH just in minutes before you realize it) but also brings a bad name to the entire crypto industry. And you cannot do much to recover those as crypto is decentralized.
This is made possible by non-KYC exchanges like “FixedFloat,” which allows rogue actors to get funds to publish contracts, steal money, and withdraw without any consequences!
This post is about 1 specific phishing attack to provide action items you can take to not fall for it and propose some product updates to Metamask, Ethereum, and possibly a new KYC service (more to come later)!
About the Drainer as a Service (DaaS)
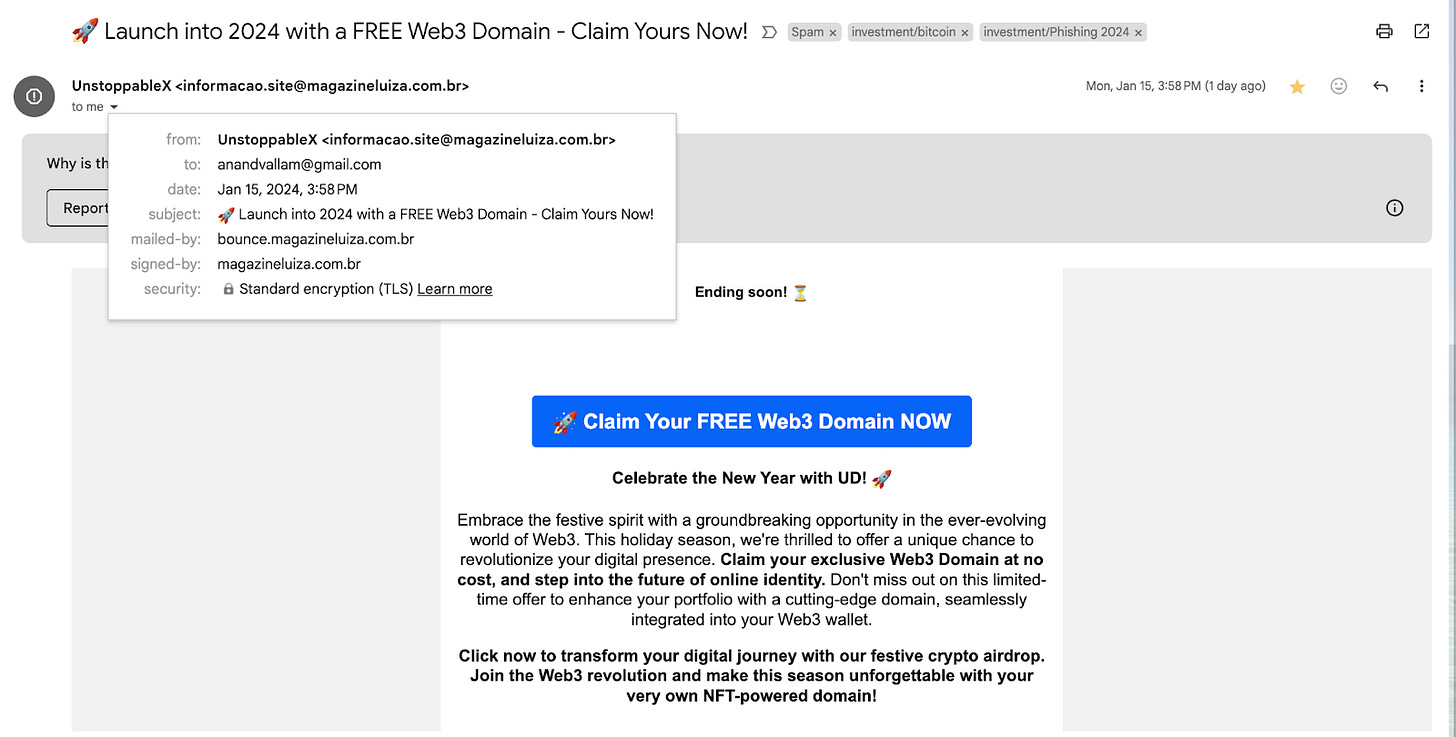
Source Of the Attack:
Email to Gmail (See below)
Attack Name:
Angle Drainer
Attack Form:
The url shows as unstoppabledomans com, but the actual URL is https://xn--unstoppabledomans-rvb com.
Action:
Once you connect your wallet to the site, it will ask you repeatedly for permissions; once you approve, it will drain all of your funds across all EVMs - BSC, ARB, Polygon, Avalanche, Optimism, FTM, Celo, Cronos, and Base. This is not only ETH but anything on top of ETH, even if it is staked.
Rogue Contract:
https://etherscan.io/address/0xf7e729e00c297d452c56a0dca163a93bb2fe6f87
This is replicated 4 more times, so there are other contract addresses that you should be careful about.
Funding Actor:
https://etherscan.io/address/0xf7e729e00c297d452c56a0dca163a93bb2fe6f87
Exchange Used for Funding:
Affiliate Address:
0x4455f284c3bB9E074305795c260a111c8F709858 is the affiliate address (the person who "rents" the drainer) (Affiliate gets 85%)
Operator Address:
0xa3aa460C12713A000a33893b024D95db80945a2F is the operator (the person who "owns" the drainer) (Operator keeps 15%)
Actions You Can Take to Protect
Always read the email headers. If the from address is suspicious, DELETE the email - don’t click on anything & most notably, report it as phishing (Gmail or email service provider AI may label it as phishing if many people report it) so that other people will benefit from your action!
Always look at the URL; if it is not something you think is legitimate, then close that tab immediately.
When you connect your Metamask or other wallet, the wallet will prompt you for permissions. READ EVERY detail on the popup before clicking approve. If you don’t understand, reject. Remember that malware scripts will repeatedly ask for approval.
If you lost your funds, I empathize with you. However, you can take some actions, like reporting to authorities so that others don’t fall victim. The chances of recovering funds are meager.
FBI IC3 Report https://www.ic3.gov/Home/ComplaintChoice
Future Proofing
Install https://revoke.cash/exploits chrome extension
https://revoke.cash/exploits - Revoke permissions and signatures for the contracts that you don’t trust
Improve products like Metamask, Ethereum, and a new KYC service. I have a lot of ideas for using crowdsourcing. to stop the attacks when they are small. More to come in the next post
If you would like updates and want to learn more about my ideas. Please subscribe to the blog.